Protect Your Remote PC with Endpoint Security
Venn is the secure workspace that can compare to a unified endpoint management (UEM) solution. Enable a smart and secure perimeter that protects your work on your PC, whether BYO or company-owned.
Perfect for companies with 50+ Unmanaged Device Users



Introducing Venn - Your Virtual Desktop Alternative
Designed for the New Era of Hybrid Work
Venn combines a Zero Trust security architecture with breakthrough technology to empower employees to use a single device for work and personal activities by creating a secure, isolated enclave for company applications and data. Say goodbye to work-only laptops.
Built to Secure BYO and Managed Devices
Venn protects work files and data from accidental or malicious exfiltration, compromise or loss on any device. Employees can browse securely without the need for a new browser.
Decide What the Users Can and Cannot Do
IT administrators are given robust controls to monitor applications and data without tracking personal activities. You can also designate work policies, remotely delete company applications and data while leaving personal data unaffected.
All the Possibilities in One Platform

BYOD Workforce
Enable freedom at work with BYOD while fully protecting company data

Zero Trust Security
Never trust but always verify right through the end to secure your endpoints

Virtual Desktop Alternative
The value of VDI or DaaS without the pain or expense

Third Party Contractors
Ensure complete security and compliance for 1099s, independent workers

Enterprise Browser Secured
Protection for SaaS and internal web apps on any device

Company VPN Replacement
Increase control over company data with a secure workspace
Venn vs.
UEM Solutions
You may think that adding a UEM solution is the best. Here’s how we compare against the entire offering when assessing individual features. This is why IT departments love us for the convenience and performance.
| VENN | UEM | |
|---|---|---|
| Unified app launcher | ||
| Endpoint device assessment & compliance | ||
| Separate work and personal computing | ||
| Gated access to work apps, files and data | ||
| Data leakage and loss prevention (DLP) | ||
| Separate, control and protect work-related network traffic from personal through a dedicated gateway with IP restrictions | ||
| Shield against active malware (including ransomware) and zero-day vulnerabilities | ||
| Device-native experience and support including mobile device parity | ||
| Personal privacy assurance | ||
| Compliance dashboard with comprehensive audit trall |
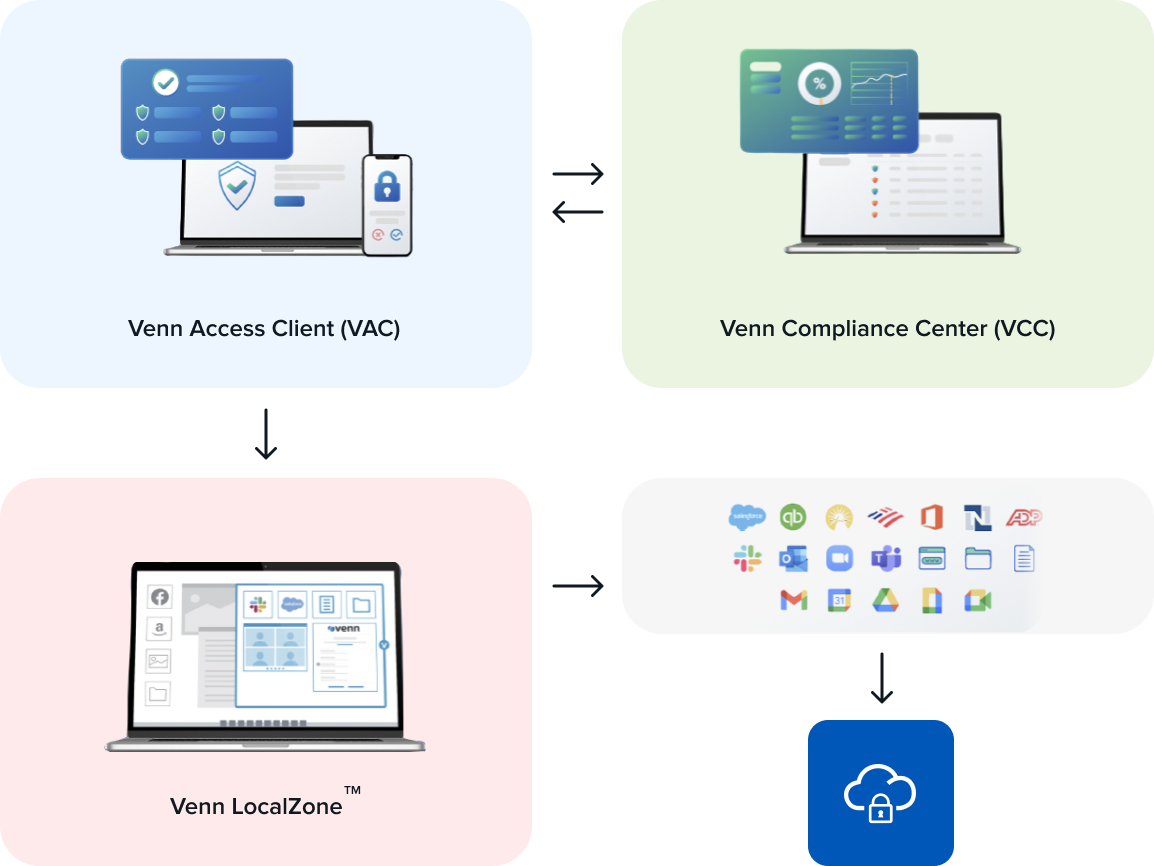
How Venn Works
1. Access Client to Check User Access
Venn leverages MFA and comprehensive device compliance checks to control user access to work apps and files running continuously.
2. Compliance Center for User Audits
IT departments can enforce technical controls, complete with audit-ready reporting through Venn’s onboarding, administration, and monitoring engine.
3. Venn Empowers User Productivity
Your users will work within a smart, secure perimeter that protects local work apps, files, and data separate from personal computing. User work apps are badged, providing a visual cue on your client’s active DLP policy.
4. Failsafe Access through Remote Hosting
Venn provides failsafe access and custom app hosting requirements through highly secured public cloud infrastructure to meet all your needs.
It's Testimony
“The Venn team were able to put a variety of applications into Venn that made for easy remote or mobile computing, and their installations were flawless. The system works seamlessly, far better than anything we have had in the past.”
- Gary Schafer, COO, Atlanta Consulting Group.








